
Procurement in 2026: Why AI-First Is No Longer Optional
ArticlesProcurement in 2026: Why AI-First Is No Longer Optional The world of procurement is changing, and not just incrementally ...

Lessons From Lands’ End At NRF: Smart Commitment Management With CLM
Articles, Customers SuccessLessons From Lands’ End at NRF: Smart Commitment Management With CLM At NRF Retail’s Big Show, Raindrop joined Lands ...

Predicts 2026: Procurement Taking Steps to Become AI-First
Articles, RecognitionGartner® Research Predicts 2026 Procurement Taking Steps to Become AI First Procurement is reinventing itself for an AI-first world ...

90-Day Plan For CPOs in 2026
ArticlesProcurement’s Old Playbook Is Breaking: Get ready the 90-Day Plan for CPOs stepping into 2026

7 Things I’d Tell A New CPO Stepping Into 2026
Articles7 Things I'd Tell A New CPO Stepping Into 2026 What top Procurement teams are doing differently as AI ...

7 Procurement Moves That Will Separate Leaders From Laggards In 2026
Articles7 Procurement Moves That Will Separate The Leaders From Laggards In 2026 What top Procurement teams are doing differently as ...

Raindrop Systems vs Basware: 7 Key Differences for 2026
ArticlesCompare Raindrop Systems and Basware: full Source-to-Pay vs P2P, AI-native vs automation, commitment visibility vs invoice visibility ...

7 Lessons Learned in 2025 About Procurement, AI, and What Comes Next
Articles7 Lessons Learned in 2025 About Procurement, AI, and what comes next What We Expected, What Surprised Us, and the ...

Raindrop Systems vs. Zip: The Difference Between Orchestration and AI- Native, Commitment-Driven Procurement
ArticlesRaindrop Systems vs. Zip: The Difference Between Orchestration and AI-Native, Commitment-Driven Procurement Key TakeawaysRaindrop Systems delivers a complete ...

Raindrop vs. JAGGAER: 6 Key Differences Defining the Future of Procurement
ArticlesRaindrop Systems vs. JAGGAER: 6 Key Differences Defining the Future of Procurement Key TakeawaysRaindrop Systems delivers AI-native procurement built ...

Raindrop Attending NRF Retail’s Big Show
Recognition, ArticlesJoin Raindrop with Lands' End at NRF' 26! This coming January 11-13, Raindrop is heading to NRF 2026: Retail ...
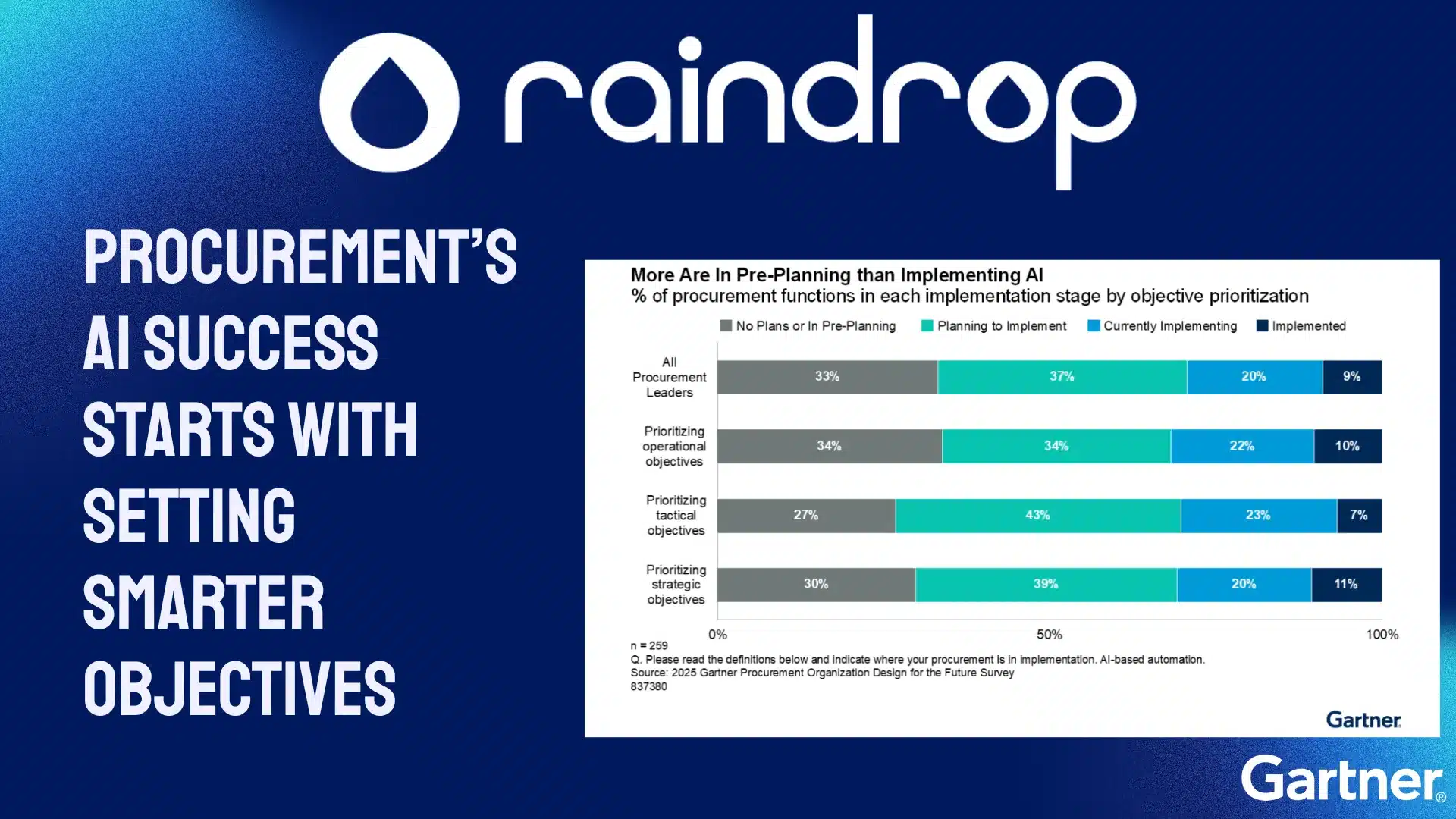
Setting Smarter Objectives for 2026: The Key to Procurement’s AI Success
Articles, RecognitionSetting Smarter Objectives for 2026: The Key to Procurement’s AI Success AI success in procurement isn’t about starting ...
